Xerar obxectos SAMBA no LDAP. Ferramentas de administración: smbldap-tools, JXplorer, LAM
Ir a la navegación
Ir a la búsqueda
Introdución
- Para que o noso dominio SAMBA funcione correctamente, é necesario inicializar o dominio cos usuarios, grupos e obxectos LDAP propios de SAMBA para almacenar toda a información do mesmo. Para iso usaremos smbldap-tools.
- Tamén veremos como administrar graficamente SAMBA: JXplorer e LAM.
smbldap-tools
- Smbldap-tools son un conxunto de scripts para manexar usuarios e grupos almacenados no directorio LDAP
- Pode ser usado tanto por usuarios como por clientes.
- Pódese:
- Engadir/modificar/eliminar usuarios/grupos no LDAP do mesmo xeito que se fai cos comandos estándar (useradd, groupadd, etc).
- Os usuarios poden cambiar o seu contrasinal e consultar información propia.
- No seguinte enlace pódese atopar máis información: https://gna.org/projects/smbldap-tools/
- A continuación amósanse os comandos asociados á utilidade
smbldap- smbldap-groupadd smbldap-groupshow smbldap-userdel smbldap-usershow smbldap-groupdel smbldap-passwd smbldap-userinfo smbldap-grouplist smbldap-populate smbldap-userlist smbldap-groupmod smbldap-useradd smbldap-usermod
Iniciar dominio samba, inserindo usuarios e grupos necesarios no ldap
- Para crear os usuarios e grupos necesarios dentro de ldap que necesita samba usarase o comando: smbldap-populate
- Antes de poder utilizar as utilidades debemos configurar dous ficheiros de configuración do paquete smbldap-tools, para que poida acceder aos datos do servidor LDAP.
- En primeiro lugar realizaremos dúas comprobacións que se recomendan no inicio do propio script e nos permitirán comprobar que o servidor samba está en execución e que a conexión co servidor LDAP é correcta:
- Comprobamos que o servidor samba está efectivamente correndo:
service smbd status
- E que o equipo xa ten un SID (Identificador de seguridade de Windows). Copiamos ese SID:
net getlocalsid SID for domain DSERVER00 is: S-1-5-21-3472892566-1518861306-3316237868
- Se as comprobacións dan un resultado correcto, podemos copiar os dous ficheiros que precisamos a /etc/smbldap-tools. E axustamos os permisos:
#Descomprimimos un dos ficheiros de configuración: zcat /usr/share/doc/smbldap-tools/examples/smbldap.conf.gz > /etc/smbldap-tools/smbldap.conf #Copiamos o outro ficheiro de configuración: cp /usr/share/doc/smbldap-tools/examples/smbldap_bind.conf /etc/smbldap-tools/ #Axustar permisos chmod 600 /etc/smbldap-tools/smbldap_bind.conf
Configuración ficheiro smbldap_bind.conf
- Este ficheiro de configuración vaille indicar a smbldap-tools cal é o usuario e contrasinal co que se accede ao servidor LDAP.
- Adaptar no ficheiro /etc/smbldap-tools/smbldap_bind.conf as liñas 10-13 ás circunstancias
- Como a chave vai en claro, é por iso que só se deu permiso de lectura escritura ao root.
# $Id$
#
############################
# Credential Configuration #
############################
# Notes: you can specify two differents configuration if you use a
# master ldap for writing access and a slave ldap server for reading access
# By default, we will use the same DN (so it will work for standard Samba
# release)
slaveDN="cn=admin,dc=iescalquera,dc=local"
slavePw="abc123."
masterDN="cn=admin,dc=iescalquera,dc=local"
masterPw="abc123."
Configuración ficheiro smbldap.conf
- Neste ficheiro /etc/smbldap-tools/smbldap.conf le os datos necesarios para poder acceder aos usuarios, grupos e máquinas do ldap.
- Configurar as liñas 36,41,60,69,80,106,111,116,121,159,165,174,194,205,211,216 como se indica.
- Ollo na liña 36 de configurar o SID do equipo do lector/a.
- Cando indicamos 4 sostenidos (####) é que ese comentario foi introducido por nós e esa liña viña activa no ficheiro orixinal.
# $Id$
#
# smbldap-tools.conf : Q & D configuration file for smbldap-tools
# This code was developped by IDEALX (http://IDEALX.org/) and
# contributors (their names can be found in the CONTRIBUTORS file).
#
# Copyright (C) 2001-2002 IDEALX
#
# This program is free software; you can redistribute it and/or
# modify it under the terms of the GNU General Public License
# as published by the Free Software Foundation; either version 2
# of the License, or (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program; if not, write to the Free Software
# Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307,
# USA.
# Purpose :
# . be the configuration file for all smbldap-tools scripts
##############################################################################
#
# General Configuration
#
##############################################################################
# Put your own SID. To obtain this number do: "net getlocalsid".
# If not defined, parameter is taking from "net getlocalsid" return
SID="S-1-5-21-3472892566-1518861306-3316237868"
# Domain name the Samba server is in charged.
# If not defined, parameter is taking from smb.conf configuration file
# Ex: sambaDomain="IDEALX-NT"
sambaDomain="IESCALQUERA"
##############################################################################
#
# LDAP Configuration
#
##############################################################################
# Notes: to use to dual ldap servers backend for Samba, you must patch
# Samba with the dual-head patch from IDEALX. If not using this patch
# just use the same server for slaveLDAP and masterLDAP.
# Those two servers declarations can also be used when you have
# . one master LDAP server where all writing operations must be done
# . one slave LDAP server where all reading operations must be done
# (typically a replication directory)
# Slave LDAP server
# Ex: slaveLDAP=127.0.0.1
# If not defined, parameter is set to "127.0.0.1"
####slaveLDAP="ldap.example.com"
# Slave LDAP port
# If not defined, parameter is set to "389"
slavePort="389"
# Master LDAP server: needed for write operations
# Ex: masterLDAP=127.0.0.1
# If not defined, parameter is set to "127.0.0.1"
####masterLDAP="ldap.example.com"
# Master LDAP port
# If not defined, parameter is set to "389"
#masterPort="389"
masterPort="389"
# Use TLS for LDAP
# If set to 1, this option will use start_tls for connection
# (you should also used the port 389)
# If not defined, parameter is set to "0"
####ldapTLS="1"
# Use SSL for LDAP
# If set to 1, this option will use SSL for connection
# (standard port for ldaps is 636)
# If not defined, parameter is set to "0"
ldapSSL="0"
# How to verify the server's certificate (none, optional or require)
# see "man Net::LDAP" in start_tls section for more details
verify="require"
# CA certificate
# see "man Net::LDAP" in start_tls section for more details
cafile="/etc/smbldap-tools/ca.pem"
# certificate to use to connect to the ldap server
# see "man Net::LDAP" in start_tls section for more details
clientcert="/etc/smbldap-tools/smbldap-tools.example.com.pem"
# key certificate to use to connect to the ldap server
# see "man Net::LDAP" in start_tls section for more details
clientkey="/etc/smbldap-tools/smbldap-tools.example.com.key"
# LDAP Suffix
# Ex: suffix=dc=IDEALX,dc=ORG
suffix="dc=iescalquera,dc=local"
# Where are stored Users
# Ex: usersdn="ou=Users,dc=IDEALX,dc=ORG"
# Warning: if 'suffix' is not set here, you must set the full dn for usersdn
usersdn="ou=usuarios,${suffix}"
# Where are stored Computers
# Ex: computersdn="ou=Computers,dc=IDEALX,dc=ORG"
# Warning: if 'suffix' is not set here, you must set the full dn for computersdn
computersdn="ou=maquinas,${suffix}"
# Where are stored Groups
# Ex: groupsdn="ou=Groups,dc=IDEALX,dc=ORG"
# Warning: if 'suffix' is not set here, you must set the full dn for groupsdn
groupsdn="ou=grupos,${suffix}"
# Where are stored Idmap entries (used if samba is a domain member server)
# Ex: groupsdn="ou=Idmap,dc=IDEALX,dc=ORG"
# Warning: if 'suffix' is not set here, you must set the full dn for idmapdn
idmapdn="ou=Idmap,${suffix}"
# Where to store next uidNumber and gidNumber available for new users and groups
# If not defined, entries are stored in sambaDomainName object.
# Ex: sambaUnixIdPooldn="sambaDomainName=${sambaDomain},${suffix}"
# Ex: sambaUnixIdPooldn="cn=NextFreeUnixId,${suffix}"
sambaUnixIdPooldn="sambaDomainName=${sambaDomain},${suffix}"
# Default scope Used
scope="sub"
# Unix password hash scheme (CRYPT, MD5, SMD5, SSHA, SHA, CLEARTEXT)
# If set to "exop", use LDAPv3 Password Modify (RFC 3062) extended operation.
password_hash="SSHA"
# if password_hash is set to CRYPT, you may set a salt format.
# default is "%s", but many systems will generate MD5 hashed
# passwords if you use "$1$%.8s". This parameter is optional!
password_crypt_salt_format="%s"
##############################################################################
#
# Unix Accounts Configuration
#
##############################################################################
# Login defs
# Default Login Shell
# Ex: userLoginShell="/bin/bash"
userLoginShell="/bin/bash"
# Home directory
# Ex: userHome="/home/%U"
userHome="/home/iescalquera/%U"
# Default mode used for user homeDirectory
userHomeDirectoryMode="700"
# Gecos
userGecos="Usuario de IES Calquera"
# Default User (POSIX and Samba) GID
defaultUserGid="513"
# Default Computer (Samba) GID
defaultComputerGid="515"
# Skel dir
skeletonDir="/etc/skel_ubuntu"
# Treat shadowAccount object or not
shadowAccount="1"
# Default password validation time (time in days) Comment the next line if
# you don't want password to be enable for defaultMaxPasswordAge days (be
# careful to the sambaPwdMustChange attribute's value)
defaultMaxPasswordAge="45"
##############################################################################
#
# SAMBA Configuration
#
##############################################################################
# The UNC path to home drives location (%U username substitution)
# Just set it to a null string if you want to use the smb.conf 'logon home'
# directive and/or disable roaming profiles
# Ex: userSmbHome="\\PDC-SMB3\%U"
userSmbHome="\\dserver00\%U"
# The UNC path to profiles locations (%U username substitution)
# Just set it to a null string if you want to use the smb.conf 'logon path'
# directive and/or disable roaming profiles
# Ex: userProfile="\\PDC-SMB3\profiles\%U"
####userProfile="\\PDC-SRV\profiles\%U"
# The default Home Drive Letter mapping
# (will be automatically mapped at logon time if home directory exist)
# Ex: userHomeDrive="H:"
userHomeDrive="Z:"
# The default user netlogon script name (%U username substitution)
# if not used, will be automatically username.cmd
# make sure script file is edited under dos
# Ex: userScript="startup.cmd" # make sure script file is edited under dos
userScript="inicio.bat"
# Domain appended to the users "mail"-attribute
# when smbldap-useradd -M is used
# Ex: mailDomain="idealx.com"
mailDomain="iescalquera.local"
##############################################################################
#
# SMBLDAP-TOOLS Configuration (default are ok for a RedHat)
#
##############################################################################
# Allows not to use smbpasswd (if with_smbpasswd="0" in smbldap.conf) but
# prefer Crypt::SmbHash library
with_smbpasswd="0"
smbpasswd="/usr/bin/smbpasswd"
# Allows not to use slappasswd (if with_slappasswd="0" in smbldap.conf)
# but prefer Crypt:: libraries
with_slappasswd="0"
slappasswd="/usr/sbin/slappasswd"
# comment out the following line to get rid of the default banner
# no_banner="1"
- Na liña 174 indicamos que os ficheiros base de cada usuario creado con smbldap-tools debe ser copiado de /etc/skel_ubuntu.
- Co cal, imos copiar de script o directorio skel_ubuntu de scripts a /etc.
cp -r /root/scripts/skel_ubuntu /etc/
Crear OUs, grupos e usuarios SAMBA no ldap: smbldap-populate
- Antes de facer nada é conveniente facer unha copia de todo o contido do LDAP, para o que podemos usar o comando slapcat:
slapcat -l backup.ldif
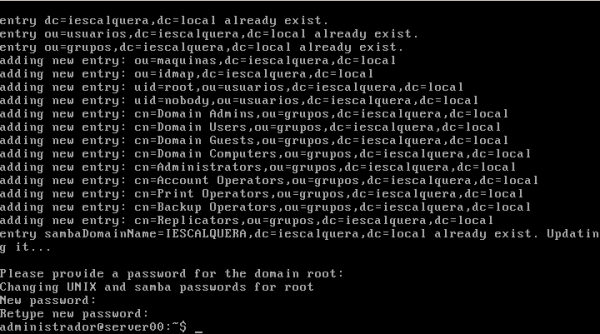
- Agora xa podemos executar o comando smbldap-populate para crear os usuarios, grupos e obxectos LDAP necesarios para o dominio samba.
smbldap-populate
- Como se pode ver na imaxe, o comando crea as unidades organizativas no LDAP necesarias para almacenar toda a información de samba e os grupos propios dun dominio Windows (Administradores do dominio, Usuarios do dominio, etc.).
- Tamén crea o usuario root no LDAP e como usuario samba, e teremos que asignarlle un contrasinal:
- Nesta imaxe, observar como se crean as OUs, Grupos e Usuarios que precisa o servizo de SAMBA.
- Observar como a OU maquinas, nesta imaxe, é creada neste proceso. No noso caso xa foi creada cando configuramos LAM.
- Comprobacións
- Unidades Organizativas
ldapsearch -x -LLL -s one -b dc=iescalquera,dc=local dn dn: cn=admin,dc=iescalquera,dc=local dn: ou=usuarios,dc=iescalquera,dc=local dn: ou=grupos,dc=iescalquera,dc=local dn: ou=maquinas,dc=iescalquera,dc=local dn: sambaDomainName=IESCALQUERA,dc=iescalquera,dc=local dn: ou=Idmap,dc=iescalquera,dc=local
- O obxecto sambaDomainName permite controlar como se van xerar os SIDs dos obxectos Windows e como se xestionarań os contrasinais, entre outras cousas.
ldapsearch -x -LLL -b sambaDomainName=IESCALQUERA,dc=iescalquera,dc=local dn: sambaDomainName=IESCALQUERA,dc=iescalquera,dc=local sambaAlgorithmicRidBase: 1000 sambaNextUserRid: 1000 sambaMinPwdLength: 5 sambaPwdHistoryLength: 0 sambaLogonToChgPwd: 0 sambaMaxPwdAge: -1 sambaMinPwdAge: 0 sambaLockoutDuration: 30 sambaLockoutObservationWindow: 30 sambaLockoutThreshold: 0 sambaForceLogoff: -1 sambaRefuseMachinePwdChange: 0 gidNumber: 1000 sambaDomainName: IESCALQUERA sambaSID: S-1-5-21-3472892566-1518861306-3316237868 sambaNextRid: 1000 uidNumber: 1000 objectClass: sambaDomain objectClass: sambaUnixIdPool
- Usuarios
ldapsearch -x -LLL -b ou=usuarios,dc=iescalquera,dc=local dn dn: ou=usuarios,dc=iescalquera,dc=local dn: ou=profes,ou=usuarios,dc=iescalquera,dc=local dn: uid=sol,ou=profes,ou=usuarios,dc=iescalquera,dc=local dn: uid=noe,ou=profes,ou=usuarios,dc=iescalquera,dc=local dn: ou=alum,ou=usuarios,dc=iescalquera,dc=local dn: ou=dam1,ou=alum,ou=usuarios,dc=iescalquera,dc=local dn: ou=dam2,ou=alum,ou=usuarios,dc=iescalquera,dc=local dn: uid=mon,ou=dam1,ou=alum,ou=usuarios,dc=iescalquera,dc=local dn: uid=tom,ou=dam1,ou=alum,ou=usuarios,dc=iescalquera,dc=local dn: uid=pia,ou=dam2,ou=alum,ou=usuarios,dc=iescalquera,dc=local dn: uid=root,ou=usuarios,dc=iescalquera,dc=local dn: uid=nobody,ou=usuarios,dc=iescalquera,dc=local
- Observar que agora temos dous novos usuarios: root e nobody.
getent passwd | tail -n 7 sol:x:10000:10000:"Profe - Sol Lua":/home/iescalquera/profes/sol:/bin/bash noe:x:10001:10000:Profe - Noe Ras:/home/iescalquera/profes/noe:/bin/bash mon:x:10002:10000:DAM1 Mon Mon:/home/iescalquera/alumnos/dam1/mon:/bin/bash tom:x:10003:10000:DAM1 Tom Tom:/home/iescalquera/alumnos/dam1/tom:/bin/bash pia:x:10004:10000:DAM2 Pia Fdez:/home/iescalquera/alumnos/dam2/pia:/bin/bash root:x:0:0:Netbios Domain Administrator:/home/iescalquera/root:/bin/false nobody:x:65534:514:nobody:/nonexistent:/bin/false
- Observar que por agora os usuarios iniciais do ldap non teñen atributos do esquema samba.
ldapsearch -x -LLL -b dc=iescalquera,dc=local uid=sol dn: uid=sol,ou=profes,ou=usuarios,dc=iescalquera,dc=local objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: sol sn:: TMO6YQ== cn:: UHJvZmUgLSBTb2wgTMO6YQ== givenName: Sol uidNumber: 10000 gidNumber: 10000 loginShell: /bin/bash mail: sol@iescalquera.local initials: SL shadowExpire: -1 gecos: "Profe - Sol Lua" homeDirectory: /home/iescalquera/profes/sol
- Pero si o teñen os 2 usuarios que se engadiron. Observar como ten un SID de Windows.
ldapsearch -x -LLL -b dc=iescalquera,dc=local uid=root dn: uid=root,ou=usuarios,dc=iescalquera,dc=local objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson objectClass: sambaSamAccount objectClass: posixAccount objectClass: shadowAccount uid: root cn: root sn: root gidNumber: 0 uidNumber: 0 homeDirectory: /home/iescalquera/root sambaLogonTime: 0 sambaLogoffTime: 2147483647 sambaKickoffTime: 2147483647 sambaPwdCanChange: 0 sambaHomePath: \\dserver00\root sambaHomeDrive: Z: sambaPrimaryGroupSID: S-1-5-21-3472892566-1518861306-3316237868-512 sambaSID: S-1-5-21-3472892566-1518861306-3316237868-500 loginShell: /bin/false gecos: Netbios Domain Administrator sambaLMPassword: B7515DC140629D41AAD3B435B51404EE sambaAcctFlags: [U] sambaNTPassword: 3EC585243C919F4217175E1918E07780 sambaPwdLastSet: 1400007291 sambaPwdMustChange: 1403895291 shadowMax: 45
- Grupos
ldapsearch -x -LLL -b ou=grupos,dc=iescalquera,dc=local dn dn: ou=grupos,dc=iescalquera,dc=local dn: cn=g-usuarios,ou=grupos,dc=iescalquera,dc=local dn: cn=g-profes,ou=grupos,dc=iescalquera,dc=local dn: cn=g-dam1-profes,ou=grupos,dc=iescalquera,dc=local dn: cn=g-dam2-profes,ou=grupos,dc=iescalquera,dc=local dn: cn=g-alum,ou=grupos,dc=iescalquera,dc=local dn: cn=g-dam1-alum,ou=grupos,dc=iescalquera,dc=local dn: cn=g-dam2-alum,ou=grupos,dc=iescalquera,dc=local dn: cn=Domain Admins,ou=grupos,dc=iescalquera,dc=local dn: cn=Domain Users,ou=grupos,dc=iescalquera,dc=local dn: cn=Domain Guests,ou=grupos,dc=iescalquera,dc=local dn: cn=Domain Computers,ou=grupos,dc=iescalquera,dc=local dn: cn=Administrators,ou=grupos,dc=iescalquera,dc=local dn: cn=Account Operators,ou=grupos,dc=iescalquera,dc=local dn: cn=Print Operators,ou=grupos,dc=iescalquera,dc=local dn: cn=Backup Operators,ou=grupos,dc=iescalquera,dc=local dn: cn=Replicators,ou=grupos,dc=iescalquera,dc=local
- Observar os novos grupos.
getent group | tail -n 16 g-usuarios:*:10000: g-profes:*:10001:noe,sol g-dam1-profes:*:10002:sol g-dam2-profes:*:10003:noe,sol g-alum:*:10004:tom,mon,pia g-dam1-alum:*:10005:tom,mon g-dam2-alum:*:10006:pia Domain Admins:*:512:root Domain Users:*:513: Domain Guests:*:514: Domain Computers:*:515: Administrators:*:544: Account Operators:*:548: Print Operators:*:550: Backup Operators:*:551: Replicators:*:552:
- Observar que os grupos que había no ldap non teñen atributos do esquema samba.
ldapsearch -x -LLL -b dc=iescalquera,dc=local cn=g-usuarios dn: cn=g-usuarios,ou=grupos,dc=iescalquera,dc=local objectClass: posixGroup cn: g-usuarios gidNumber: 10000
- Pero observar que os grupos engadidos con smbldap-populate si teñen a tributos do esquema samba:
ldapsearch -x -LLL -b dc=iescalquera,dc=local cn="Domain A*" dn: cn=Domain Admins,ou=grupos,dc=iescalquera,dc=local objectClass: top objectClass: posixGroup objectClass: sambaGroupMapping cn: Domain Admins gidNumber: 512 memberUid: root description: Netbios Domain Administrators sambaSID: S-1-5-21-3472892566-1518861306-3316237868-512 sambaGroupType: 2 displayName: Domain Admins
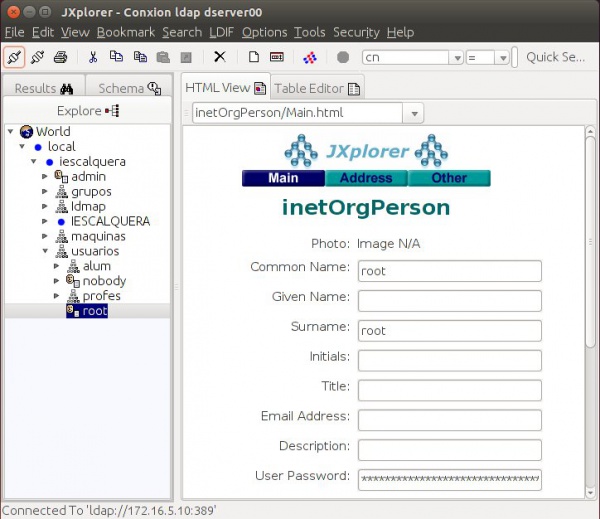
JXplorer
- Dende a ferramenta JXplorer podemos administrar os usuarios, grupos e OUs do ldap.
- Podemos ver os novos obxectos creados con smbladap-populate.
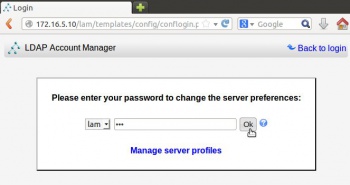
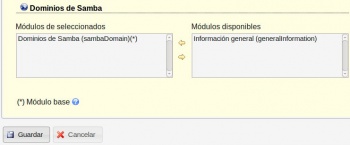
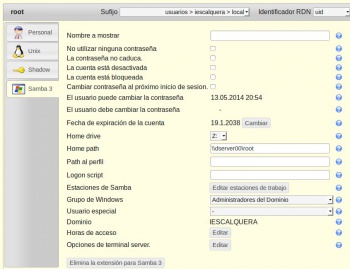
Ldap Account Manager: LAM
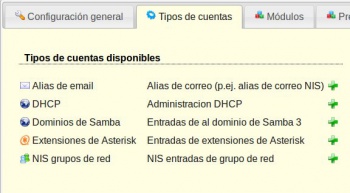
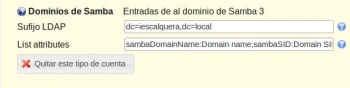
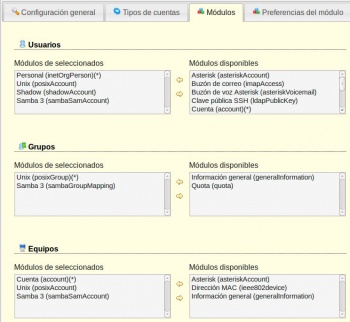
- Dende LAM para administrar os atributos SAMBA dos obxectos precisamos configurar os módulos de LAM antes de entrar a administrar o ldap.
- Logo, no seguinte punto, administraremosos usuarios e os grupos.
- Configurar LAM